Appendix C: NIST Cybersecurity Framework Basics
Health Care and Public Health Sector Cybersecurity Framework Implementation Guide
NIST Cybersecurity Framework Structure and Terminology
For an industry, sector, or organization to implement the NIST Cybersecurity Framework one must understand that it relies on existing standards, guidance, and best practices to achieve specific outcomes meant to help organizations manage their cybersecurity risk.[69] The NIST Cybersecurity Framework provides a common language and mechanism to:
- Describe their current cybersecurity posture
- Describe their target state for cybersecurity
- Identify and prioritize opportunities for improving the management of risk
- Assess progress toward the target state
- Foster communications among internal and external stakeholders
The NIST Cybersecurity Framework is intended to complement rather than replace an organization's existing business or cybersecurity risk management process and cybersecurity program. Instead, organizations should use its current processes and leverage the Framework to identify opportunities to improve an organization's management of cybersecurity risk. Alternatively, an organization without an existing cybersecurity program can use the Framework as a reference to establish one. In other words, the NIST Cybersecurity Framework provides an overarching set of guidelines to critical infrastructure industries to provide a minimal level of consistency as well as depth, breadth, and rigor of industry's cybersecurity programs.
The NIST Cybersecurity Framework consists of three main components: Framework Core, Framework Implementation Tiers, and the Framework Profile.[70] Each component is designed to strengthen the connection between business drivers and cybersecurity activities. The Core, Tiers, and Profiles represent the key structure of the Framework, which this document frequently references.
Core
The NIST Cybersecurity Framework Core is a set of cybersecurity activities, desired outcomes, and applicable references that are common across critical infrastructure sectors.[71] The Core presents industry standards, guidelines, and practices in a manner that allows for communication of cybersecurity activities and outcomes across the organization from the executive level to the implementation/operations level.
The four Core elements are:[72]
Functions: Functions provide five focus areas that can shape cybersecurity activities at a strategic level for an organization’s cybersecurity management. The Functions aid an organization in expressing its management of cybersecurity risk by organizing information, enabling risk management decisions, addressing threats, and improving by learning from previous activities. Although the NIST Cybersecurity Framework leverages the risk management framework (RMF) outlined in NIST’s Special Publication 800-series documents, it is different in several respects. The key difference here is that the NIST Cybersecurity Framework Functions categorize cybersecurity requirements using what is essentially an incident management process. The five Functions are:[73]
-
Identify - Develop the organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities. The activities in the Identify Function lay the foundation for effective Framework use.
-
Protect - Develop and implement the appropriate safeguards to ensure delivery of critical infrastructure services. The Protect Function limits potential cybersecurity events.
-
Detect - Develop and implement the appropriate activities to identify the occurrence of a cybersecurity event, enabling the timely discovery of cybersecurity incidents.
-
Respond - Develop and implement the appropriate activities to take action regarding a detected cybersecurity event. The Respond Function supports the ability to contain the impact of a potential cybersecurity event.
-
Recover - Develop and implement appropriate activities for resilience planning and restore any capabilities or services impaired by the cybersecurity event.[74]
When considered together, these Functions provide a high-level, strategic view of the lifecycle of an organization’s management of cybersecurity risk.
Categories: The Framework decomposes Functions into Categories, which are cybersecurity outcomes that closely relate to programmatic needs and specific activities. Categories add an additional layer of specificity within the Core Functions. In the Identify Function for instance, categories include Governance, Business Environment, and Asset Management.
Subcategories: Subcategories further break down a particular Category into specific outcomes of a technical or management activity. Subcategories also provide a set of results that help support achievement of each Category’s outcomes. Examples of Subcategories include, “External information systems are catalogued,” “Data-at-rest is protected,” and, “Notifications from detection systems are investigated.”
In a general sense, an informative reference, sometimes called a mapping, indicates how one document relates to another document. The National Cybersecurity Online Informative References Program[75] is a NIST effort to facilitate subject matter experts (SMEs) in defining standardized online informative references (OLIRs) between elements of their cybersecurity, privacy, and workforce documents and elements of other cybersecurity, privacy, and workforce documents like the Cybersecurity Framework. The OLIR Catalog provides an interface for Developers and Users to view Informative References and analyze Reference Data between various standards and practices commonly used across the HPH and other critical infrastructure sectors.[76]
Implementation Tiers
Implementation Tiers provide context on how an organization views cybersecurity risk and the processes in place to manage that risk.[77] Tiers describe the degree to which an organization's cybersecurity risk management practices exhibit the characteristics defined in the Framework (e.g., risk and threat aware, repeatable, and adaptive). The Tiers characterize an organization's practices over a range, from Partial (Tier 1) to Adaptive (Tier 4). These Tiers reflect a progression from informal, reactive responses to approaches that are agile and risk informed. During the Tier selection process, an organization should consider its current risk management practices, threat environment, legal and regulatory requirements, business/mission objectives, and organizational constraints.
Profiles
NIST Cybersecurity Framework Profiles represent outcomes based on business needs that an organization has selected from the Framework Categories and Subcategories.[78] A profile can be characterized as the alignment of standards, guidelines, and practices to the NIST Cybersecurity Framework Core in a particular implementation scenario. Profiles can be used to identify opportunities for improving cybersecurity posture by comparing a “Current" Profile (the “as is" state) with a “Target" Profile (the “to be" state). To develop a Profile, an organization can review all of the Categories and Subcategories and based on business drivers and a risk assessment, determine which are most important; they can add Categories and Subcategories as needed to address the organization's risks. The Current Profile can then be used to support prioritization and measurement of progress toward the Target Profile, while factoring in other business needs, including cost-effectiveness and innovation. Profiles can be used to conduct self-assessments and communicate within an organization or between organizations.
Refer to the
Framework for Improving Critical Infrastructure Cybersecurity for more information on the NIST Cybersecurity Framework.
Generic Implementation
Within the HPH Sector, various organizations already have risk management programs of some type with varying levels of maturity. In many cases, organizations' risk assessment activities already align with the NIST Cybersecurity Framework, and implementation is largely a matter of translating elements of current activities and programs to the NIST Cybersecurity Framework Core and Implementation Tiers.
NIST recommends using a seven-step process for implementation.[79]
- Step 1: Prioritize and scope organizational components for framework adoption
- Step 2: Identify systems and existing risk management approaches within the scope
- Step 3: Create a current risk management profile (Current Profile)
- Step 4: Conduct a risk assessment
- Step 5: Create a desired risk management profile based on assessment results (Target Profile)
- Step 6: Develop a prioritized action plan of controls and mitigations (Action Plan)
- Step 7: Implement the Action Plan
The diagram provided in Figure 6 below shows these steps and the key activities completed within each step. The approach can and should be an iterative process, repeated to address the evolving risk environment.
Figure 6. Generic Implementation Process
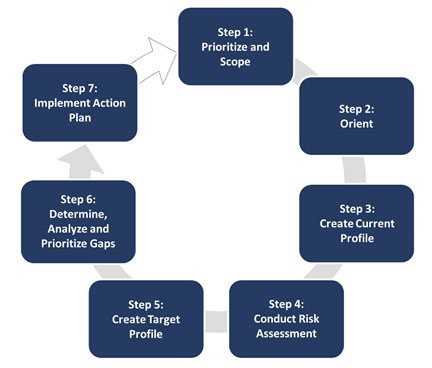
In addition to these steps, implementation should include a plan to communicate progress to appropriate stakeholders, such as senior management, as part of the organization’s risk management program. Each step of the process should provide feedback and validation to previous steps, which can facilitate process improvement and increase the overall effectiveness and efficiency of the process. Comprehensive and well-structured feedback and communication plans are a critical part of any cybersecurity risk management approach.
The following provides additional context, explanation, and guidance from the NIST Cybersecurity Framework document for each step.
The organization identifies its business/mission objectives and high-level organizational priorities. With this information, the organization makes strategic decisions regarding cybersecurity implementations and determines the scope of systems and assets that support the selected business line or process. The Framework can be adapted to support the different business lines or processes within an organization, which may have different business needs and associated risk tolerance.[80]
The organization identifies related systems and assets, regulatory requirements, and overall risk approach. The organization then identifies threats to, and vulnerabilities of, those systems and assets.
The organization develops a Current Profile by indicating which Category and Subcategory outcomes from the Framework Core are currently being achieved.
The organization analyzes the operational environment in order to discern the likelihood of a cybersecurity event and the impact that the event could have on the organization. It is important that organizations seek to incorporate emerging risks along with threat and vulnerability data to facilitate a robust understanding of the likelihood and impact of cybersecurity events. This assessment could be guided by the organization’s overall risk management process or previous risk assessment activities.
The organization creates a Target Profile that focuses on the assessment of the Framework Categories and Subcategories describing the organization's desired cybersecurity outcomes. Organizations also may develop their own additional Categories and Subcategories to account for unique organizational risks. The organization may also consider influences and requirements of external stakeholders such as sector entities, customers, and business partners when creating a Target Profile.
The organization compares the Current Profile and the Target Profile to determine gaps. Next, it creates a prioritized action plan to address those gaps that draws upon mission drivers, a cost/benefit analysis, and understanding of risk to achieve the outcomes in the Target Profile. The organization then determines resources necessary to address the gaps. Using Profiles in this manner enables the organization to make informed decisions about cybersecurity activities, supports risk management, and enables the organization to perform cost-effective, targeted improvements.
The organization determines which actions to take for any existing gaps identified in the previous step. It then monitors its current cybersecurity practices against the Target Profile. For further guidance, the Framework identifies example Informative References regarding the Categories and Subcategories, but organizations should determine which standards, guidelines, and practices work best for their needs, including those requirements that are sector or organization specific.
An organization may repeat the steps as needed to continuously assess and improve its cybersecurity. For instance, organizations may find that more frequent repetition of the Orient step improves the quality of risk assessments. Furthermore, organizations may monitor progress through iterative updates to the Current Profile, subsequently comparing the Current Profile to the Target Profile. Organizations may also utilize this process to align their cybersecurity program with their desired Framework Implementation Tier.
<< Back Next >>
69 NIST (2018, Apr 16), p. 2.
70 Ibid., pp. 4-5
71 NIbid., p. 2.
72 Ibid., pp. 4-5.
73 Ibid., pp. 6
74 NIST (2022c).
Cybersecurity Framework: The Five Functions.
75 Keller, N., Quinn, S., Scarfone, K., Smith, M., and Johnson, V. (2020, Nov).
National Online Informative References (OLIR) Program and OLIR Uses (NISTIR 8278). Gaithersburg, MD: NIST.
76 NIST (2022a).
77 NIST (2018, Apr 16), pp. 8-11.
78 Ibid., p. 11
79 Ibid., pp. 13-15
80 For more information on risk tolerance, see NIST (2020, Oct).

