Table 6. Step 6: Gap Analysis Inputs, Activities, and Outputs
-
Current Profile
-
Target Profile
-
Organizational objectives
-
Impact to critical infrastructure
-
Gaps and potential consequences
-
Organizational constraints
-
Risk management strategy
-
Risk assessment/analysis reports
-
Informative Reference(s)
|
- Analyze gaps between Current and Target Profiles in organization's context
- Evaluate potential consequences from gaps
- Determine which gaps need attention
- Identify actions to address gaps
- Perform cost-benefit analysis (CBA) or similar analysis on actions
- Prioritize actions (CBA or similar analysis) and consequences
- Plan to implement prioritized actions
|
-
Prioritized gaps and potential consequences
- Prioritized implementation plan
|
The organization evaluates its Current Profile and Implementation Tier against its Target Profile and Target Implementation Tier and identifies any gaps. When mapping back to the NIST Cybersecurity Framework, a gap exists when there is a desired Category or Subcategory outcome in the Target Profile or program characteristic in the Target Implementation Tier that is not currently achieved by the organization's existing cybersecurity and risk management approach, and when current practices do not achieve the outcome to the degree of satisfaction required by the organization's risk management strategy.
After controls are specified by an organization to ensure risk is controlled to a level formally deemed acceptable by executive leadership, the most common way of dealing with (i.e., treating) deficiencies observed with the implementation and management of those controls is to remediate them. This reduces risk to an acceptable level, a process referred to as mitigation.
Cybersecurity Risk Management
Although ostensibly intended for U.S. Federal Agencies, NIST provides excellent guidance on how to manage cybersecurity risk that is also applicable to private sector organizations. For example, NIST SP 800-39 provides guidance for an integrated, organization-wide program for managing information security risk to organizational operations (i.e., mission, functions, image, and reputation), organizational assets, individuals, and other organizations resulting from the operation and use of information systems. It also provides a structured, yet flexible approach for managing information security risk that is intentionally broad-based, with the specific details of assessing, responding to, and monitoring risk on an ongoing basis provided by other supporting NIST security standards and guidelines.[47]
Cybersecurity in Enterprise Risk Management (ERM)
Cybersecurity risk is often managed independently of other types of business risk due to generally dissimilar oversight and reporting requirements;[48] however, it is generally in the best interest of an organization to manage all business risk holistically as part of a broader ERM program, which will help 'min-max' its return on investment and reduce strategic, operations, reporting, and compliance risk, as shown in Figure 4.[49]
Figure 4. Relating Cybersecurity Risk to Other Forms of Business Risk
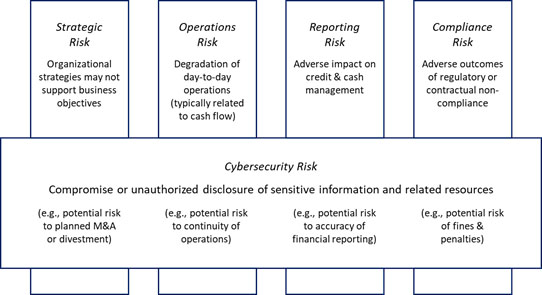
Subsequently, organizations should ensure they identify, evaluate, and communicate cybersecurity risk in the same way other business risks are communicated to senior decision makers. In addition to developing a specific plan of action to address control gaps, organizations should also track associated risks in one or more cybersecurity risk registers, which in turn should be integrated with other risk registers (e.g., financial, and regulatory compliance) to create an Enterprise Risk Register (ERR).[50] The ERR should then be used to create an enterprise risk profile to help senior decision-makers determine which risks should be addressed, to whom responsibilities should be assigned, and how resources should be allocated.[51] Note the risk profile should be updated whenever the underlying cybersecurity risk registers are updated, e.g., after a risk assessment or when risk responses are completed.[52]
Scoring and Reporting
By leveraging an implementation maturity model such as the one presented by NIST[53] and applying an ordinal scoring model, it's possible to evaluate and score how well an organization achieves the outcomes specified by the NIST Cybersecurity Framework's Core Subcategories based on the aggregate of the controls assigned.[54]
The NIST model uses five levels of implementation maturity (ML), as shown in Table 7.
Table 7. NIST Maturity Levels
1 – Policies
|
Does the organization know what it needs to do?
|
2 – Procedures
|
Does the organization know how to do it?
|
3 – Implementation
|
Has the organization done it?
|
4 – Test
|
Does the organization keep track of it and fix it if something goes wrong?
|
We present two types of maturity scales based on a ‘traditional’ bell-shaped model and a left-skewed bell-shaped ‘academic’ model based on similar risk reporting models. Although the traditional model is best used for communicating compliance to external stakeholders, the academic model provides a very intuitive approach to understanding compliance when presented as grades, reminiscent of the model used by the federal government to report security status of federal agencies.
Table 8 on the following page provides the intervals for both models:
Table 8. Achievement Scales
|
Level of Compliance 3 |
Range 4 |
Level of Compliance 5 |
Range 6
|
|
Very High |
96-100 |
'A' |
90-100 |
|
High |
80-95 |
'B' |
80-89 |
|
Moderate |
21-79 |
'C' |
70-79 |
|
Low |
5-20 |
'D' |
60-69 |
|
Very Low |
0-4 |
'F' |
0-59 |
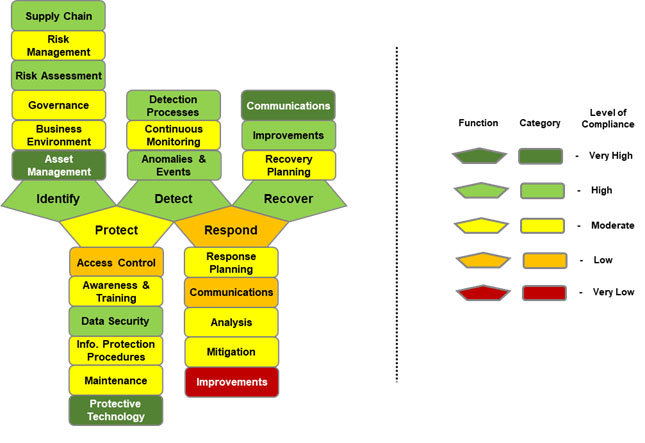
A manually constructed scorecard based on the NIST Cybersecurity Framework Functions and Categories using a traditional scoring model is provided in Figure 5 on the next page. In this example, specific controls mapped to each of the NIST Cybersecurity Framework’s Core Subcategories would have been individually evaluated and scored (potentially using the approach just described), and those scores would be aggregated and averaged according to how they mapped to the Subcategories. The Subcategory scores would then be aggregated and averaged for their ‘parent’ Categories and reflected as shown in Figure 5. Category scores would be similarly aggregated, averaged, and displayed for their respective Functions.
Figure 5. Example NIST Cybersecurity Framework Scorecard
Corrective Action Plans
Deficiencies or ‘gaps’ in a control’s implementation should be corrected immediately or a Corrective Action Plan (CAP) should be developed that outlines the activities and technology required to remediate the gap.

